Overcoming the Cybersecurity Dangers of BYOD
In today’s high tech world, nearly everyone you meet owns a smartphone, tablet, or laptop computer.
And they use these devices for work.
While that is a convenience for employees and employers, for those who sit in the CIO’s chair, BYOD is a source of constant headaches. Data breaches can happen at any time, and personal devices ensure a loss of control that keeps data security teams up at night.
Personal Device Use by the Numbers
Recent survey data from Finn Partners paints a grim picture surrounding the use of personal security devices by employees. While a full 55 percent of employees BYOD, only 26 percent change log-in credentials on a monthly basis. Only 25 percent of these employees update the security protocols and operating systems on their devices each month.
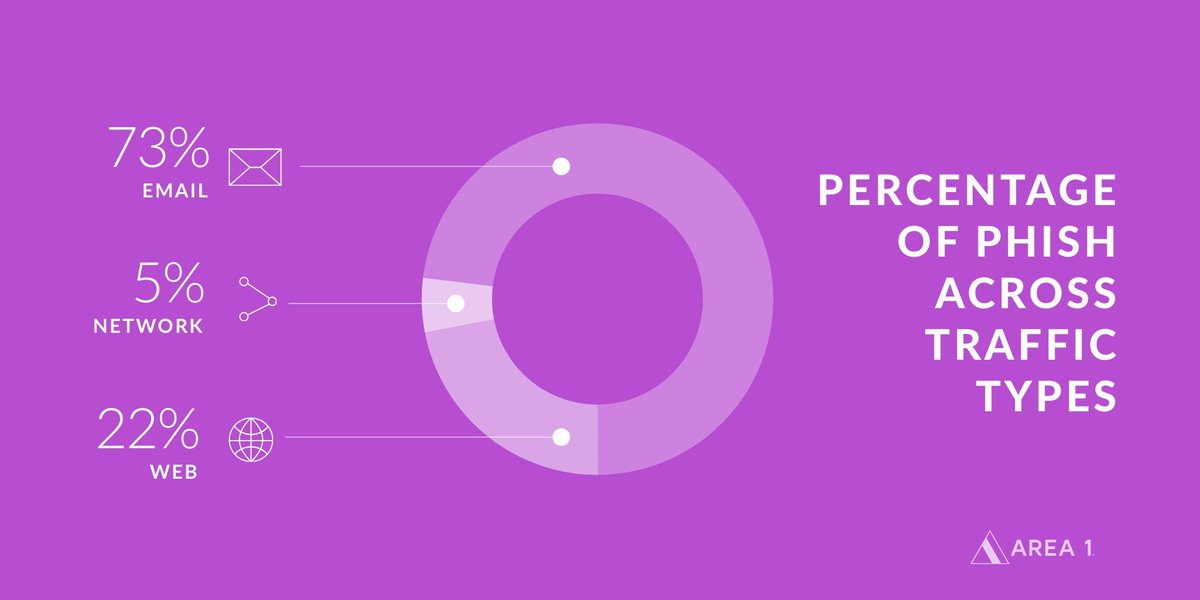
When you look at phishing, the root cause of 95 percent of all breaches, the numbers grow darker still. In the Finn Partners survey, nearly 40 percent of employees admitted to clicking on a link or opening an attachment from a sender they didn’t recognize. Two out of five employees admit to putting their companies at risk both in the office and on their own devices. It’s no surprise that one in three of these employees reports being victims of a cyber-attack or data breach.
Solutions in Sight
There are a number of steps an organization can take to minimize risks. IT departments can limit access to company documents and records for smartphones and tablets. They can also ensure that all data downloaded is fully encrypted. Moreover, cybersecurity professionals can enforce remote wipe policies and passcode locks on all devices being used for company use.
But in an era where nearly 40 percent of employees will click a link or open an attachment from someone they don’t know, cybersecurity teams will need to take solutions to the next level. The best solution is to stop phishing attacks at the source.
Take the Next Step in Cybersecurity
To accomplish this, use preemptive anti-phishing solutions that stop attacks from even entering employee’s devices. This reduces the likelihood of compromisation of an organization’s sensitive data. Consequently, taking this one step will eliminate nearly all cybersecurity threats to a company.
Area 1 Security stops phishing attacks with their anti-phishing solution, Area 1 Horizon. It protects your organization across all traffic vectors, and you’ll only be paying for phish they catch. Area 1 Horizon allows security professionals with BYOD policies to enjoy a better night’s sleep.